Pwndrop on Linode

When I first ran across PwnDrop, I was intrigued at what the developers had in mind with it. For instance, if you're a white-hat hacker and are looking to share exploits safely with your client, you might use a service like PwnDrop. If you're a journalist communicating with, well, just about anyone who is trying to keep their identity secret, you might use a service like PwnDrop.
In this tutorial, we're going to look at how easy it is to set up and use in just a few minutes.
Prerequisites for PwnDrop in Docker
First things first, you’ll need a Docker server set up. Linode has made that process very simple and you can set one up for just a few bucks a month and can add a private IP address (for free) and backups for just a couple bucks more per month.
Another thing you’ll need is a domain name, which you can buy from almost anywhere online for a wide range of prices depending on where you make your purchase. Be sure to point the domain's DNS settings to Linode. You can find more information about that here: https://www.linode.com/docs/guides/dns-manager/
You’ll also want a reverse proxy set up on your Docker Server so that you can do things like route traffic and manage SSLs on your server. I made a video about the process of setting up a Docker server with Portainer and a reverse proxy called Nginx Proxy Manager that you can check out here: https://www.youtube.com/watch?v=7oUjfsaR0NU
Once you’ve got your Docker server set up, you can begin the process of setting up your PwnDrop password manager on that server.
There are 2 primary ways you can do this:
- In the command line via SSH.
- In Portainer via the Portainer dashboard.
We're going to take a look at how to do this in Portainer so that we can have a user interface to work with.
Head over to http://your-server-ip-address:9000 and get logged into Portainer with the credentials we set up in our previous post/video.
On the left side of the screen, we're going to click the "Stacks" link and then, on the next page, click the "+ Add stack" button.
This will bring up a page where you'll enter the name of the stack. Below that that you can then copy and paste the following:
version: "2"<br></br>services:<br></br> pwndrop:<br></br> image: lscr.io/linuxserver/pwndrop:latest<br></br> container_name: pwndrop<br></br> environment:<br></br> - PUID=1000<br></br> - PGID=1000<br></br> - TZ=America/Denver<br></br> - SECRET_PATH=/dbtech #optional<br></br> volumes:<br></br> - /home/docker/pwndrop:/config<br></br> ports:<br></br> - 8080:8080<br></br> restart: unless-stopped<br></br> networks:<br></br> nginxproxymanager_default:<br></br><br></br>networks:<br></br> nginxproxymanager_default:<br></br> external: true
This Docker compose file / stack tells the system to download the latest linuxserver/pwndrop image to the Docker server, name the container "pwndrop", attach it to the "nginxproxymanager_default" network, mount it to the directory "home/docker/pwndrop", and make it available on the docker server's port 8080.
You can change the path of where you'd like to store the PwnDrop data if you'd like. Just make sure that the folder has the correct permissions to be written to.
Als, the secret path variable is important as it will be what you tack onto the end of your URL to access the dashboard. Choose this variable wisely.
Once you're happy with the settings here, we can deploy the container by clicking the button that says "Deploy the stack".
This will start the process of downloading and deploying FileRun on your server. You'll know that the container has been deployed once the page reloads and you see your running containers.
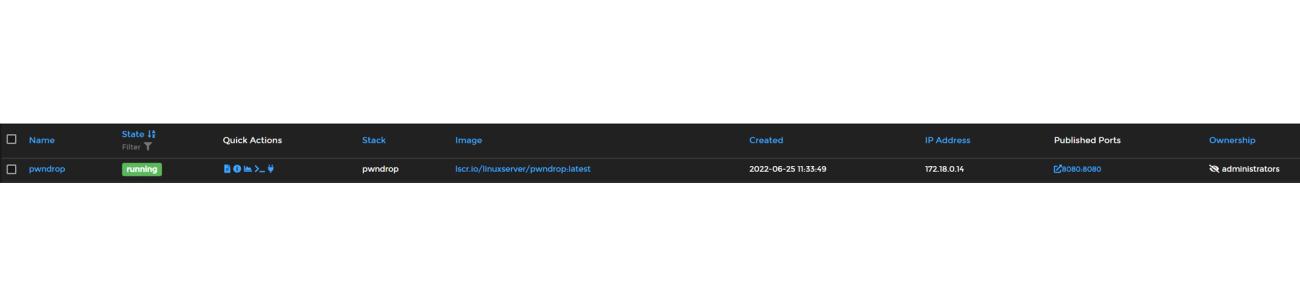
Now you can go to http://your-server-ip-address:90 and you should be able to see the login screen for PwnDrop.
STOP
In order for you to actually be able to use PwnDrop, it needs a domain name and SSL.
Setting up a domain and SSL
Head back over to your Linode dashboard and go to "Domains". Then find the domain that you added to your account. Click it and then look for the CNAME section of the domain management.
Add a CNAME to your domain by entering a hostname entry for what you'd like your subdomain to be. In the example video, I entered "pwn" (without the quotes). Below that, I entered the @ symbol in the "Alias to" box and then clicked "Save".
Now that you have that done, we can head over to Nginx Proxy Manager and set up our SSL and domain.
Now you can go to http://your-server-ip-address:81 and you should be able to see the login screen for Nginx Proxy Manager.
The default credentials for Nginx Proxy Manager are:
Email: admin@example.com
Password: changeme
Enter those credentials (or yours if you've updated them) to login to your Nginx Proxy Manager instance.
Click on the tab at the top of the page that says "SSL Certificates" and then click on the "Add SSL Certificate" button near the top right of the page.
Next, click the "Let's Encrypt" option.
On the pop-up window that appears, enter the full URL of the domain you'd like to secure and press the "Enter" key on your keyboard. In this example, you would enter https://pwn.yourdomain.com.
Once you've entered your URL, click the "Test Server Reachability" button right below that. If you get an error message, be sure to correct the issue and try again. If no errors are returned, make sure the email address on the page is correct, then read and agree to the Let's Encrypt Terms of Service and click the "Save" button.
It may take a minute or two for the system to generate and install the key, but when it's done, the page will reload and you'll be able to see all of the available SSLs in Nginx Proxy Manager.
Now that we have our SSL set up on our system, we can click the "Hosts" tab across the top of the page. Then click the "Proxy Hosts" option that shows up in the sub-menu.
Locate the "Add Proxy Host" button near the top right of the page and click it.
A new window will pop up and we're going to fill in some options to configure our domain.
Enter the domain or subdomain you just created the SSL for.
Leave the Scheme as http.
Enter the IP address of your container. This can be found in Portainer:
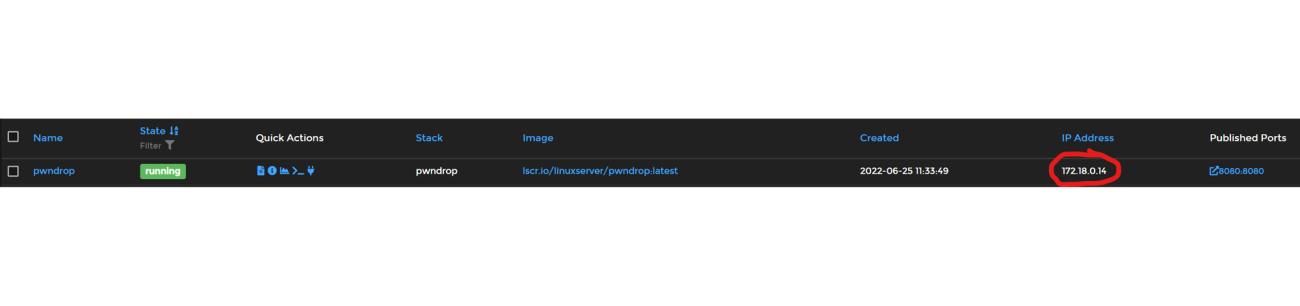
For the "Forward Port" textbox, enter the container port. In this case it's 8080.
Click the options for "Cache Assets," "Block Common Exploits," and "Websocket Support."
Now click the "SSL" tab on the top of the pop up window.
You'll see a dropdown that says "SSL Certificate" and, below that, "None."
Click "None" and then select the SSL you created in the previous steps.
Now check the 4 options that are below that, then read and agree to the Let's Encrypt TOS and then click Save.
After a moment, the page will reload and you should see your new entry in the Proxy Hosts page of Nginx Proxy Manager.
Create Your Account
Now you can head over to your new URL in your browser.
You should be prompted to create an account. Enter a username and password and click the submit button.
That's it. You've created your account.
At this point, you can now login to your account and start sharing files.
PwnDrop has some cool features that allows you to have alternate files and URLs available at the click of a "facade" button. You can set up facade files, which will be served instead of the original file whenever you feel like it. I'm sure you can figure out all sorts of uses for something like this.
Wrap Up
That's it! You should be good to go and you should be able to use your new semi-self-hosted file hosting service for red teamers, allowing you to easily upload and share payloads over HTTP and WebDAV.
You can watch the tutorial here:






